EyeQ Dot Net leads the way in advanced cybersecurity, protecting businesses globally. As your trusted defender, we shield you from emerging threats with cutting-edge solutions.


An Intrusion Prevention System (IPS) is a network security tool designed to detect and prevent identified threats.
Essential for protecting networks from unauthorized access, malware, and other cyber threats. Complements other network security measures like firewalls and intrusion detection systems.
Actively blocks malicious activities and unauthorized access, Reduces the risk of data breaches and cyber-attacks.
Provides real-time threat detection and automated responses, Enhances overall security posture by integrating with existing security measures.
A network intrusion protection system (NIPS) is an umbrella term for a combination of hardware and software systems that protect computer networks from unauthorized access and malicious activity. A NIPS helps organizations detect and respond to potential threats in real time, maintaining the integrity and confidentiality of data.
These systems are placed inline with the flow of network traffic, where they examine network packets, protocols and patterns to identify suspicious behavior, such as unauthorized access attempts, malware infections and data breaches. A NIPS detects problems and alerts administrators to potential issues. In doing so, it plays a crucial role in minimizing the impact of cyber attacks and fortifying network defenses.
A wireless intrusion detection system (WIDS) monitors the radio spectrum for the presence of unauthorized, rogue access points and the use of wireless attack tools. The system monitors the radio spectrum used by wireless LANs, and immediately alerts a systems administrator whenever a rogue access point is detected. Conventionally it is achieved by comparing the MAC address of the participating wireless devices.
Rogue devices can spoof MAC address of an authorized network device as their own. New research uses fingerprinting approach to weed out devices with spoofed MAC addresses. The idea is to compare the unique signatures exhibited by the signals emitted by each wireless device against the known signatures of pre-authorized, known wireless devices.
The Host-based Intrusion Prevention System (HIPS) protects your system from malware and unwanted activity attempting to negatively affect your computer. HIPS utilizes advanced behavioral analysis coupled with the detection capabilities of network filtering to monitor running processes, files and registry keys. HIPS is separate from Real-time file system protection and is not a firewall; it only monitors processes running within the operating system.
Network Behavior Analysis (NBA), also known as "Behavior Monitoring", is the process of collecting and analyzing internal network data to detect malicious or unusual activity, such as policy violations, Denial-of-Service, worms, or malware.
It can be implemented on a hardware appliance or as a software package. The traffic flows, which are the primary data for NBA analysis, are typically collected directly by sensors (also known as analyzers) or provided in a traffic flow data format by routers or other networking devices. There are several flow data format standards, the most common of which are NetFlow and sFlow.
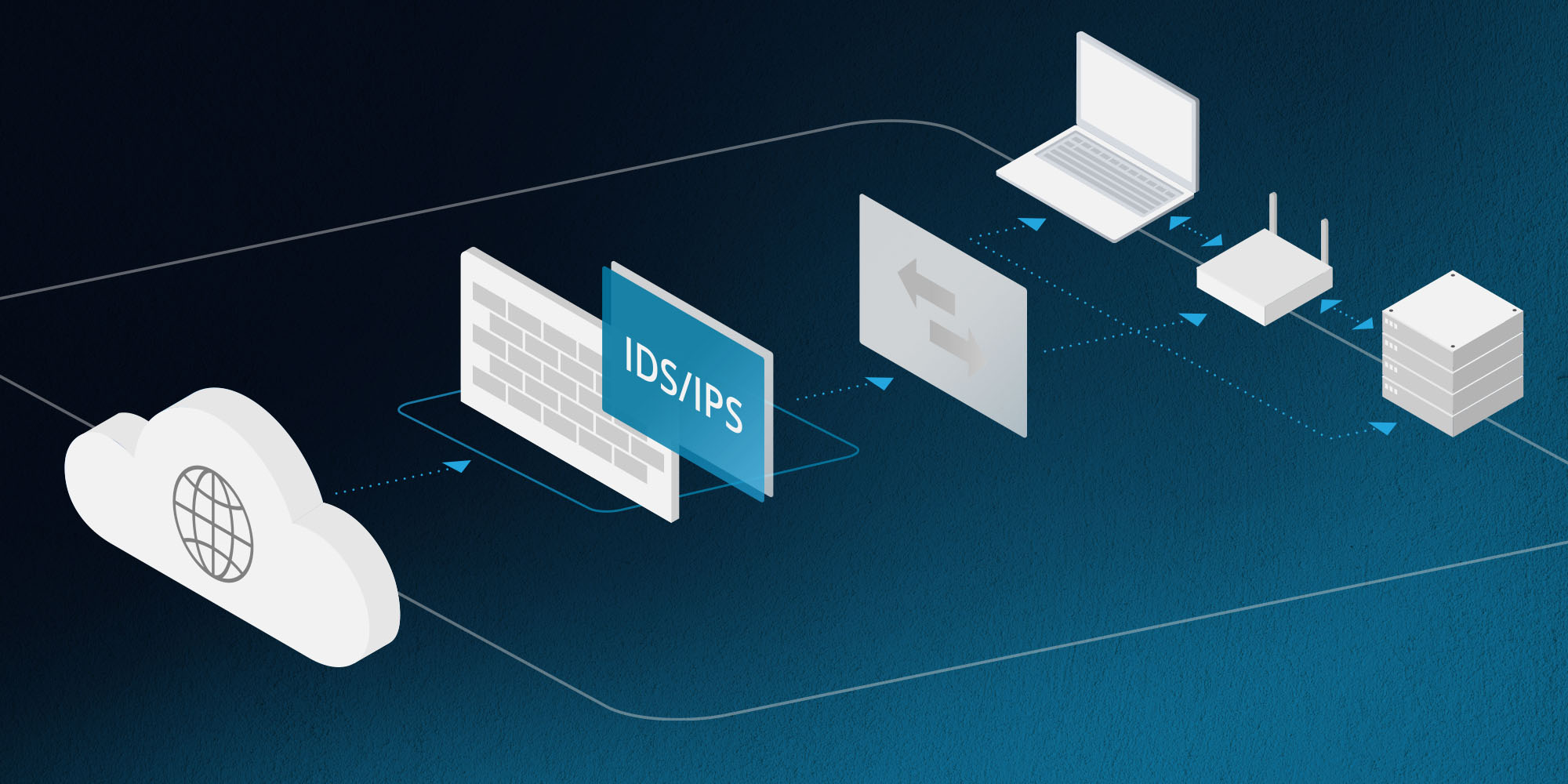
There are a number of benefits to using intrusion prevention system monitoring for network security. Let’s take a closer look at the top four pluses to utilising an IPS within your organisation:
Real-world use cases of intrusion prevention systems in various industries.
Protects sensitive business data and intellectual property.
Ensures the security of patient data and medical records.
Safeguards financial transactions and customer information.
Protects classified information and critical infrastructure.
An IPS is crucial for protecting networks from unauthorized access, malware, and other cyber threats by providing real-time threat detection and automated responses.
While an IDS monitors and alerts on potential threats, an IPS actively blocks and mitigates those threats to prevent damage.
No, an IPS complements a firewall by adding an additional layer of security, but it does not replace the need for a firewall.
The main types are Network-Based IPS (NIPS), Host-Based IPS (HIPS), Wireless IPS (WIPS), and Network Behavior Analysis (NBA).
Firewalls filter traffic based on predefined rules, while IPS analyzes and blocks malicious activity in real-time, providing comprehensive network security.
NIPS monitors and analyzes network traffic for suspicious activities across the entire network.
Benefits include enhanced security, automated threat responses, regulatory compliance, and reduced risk of data breaches.
By providing real-time monitoring, threat detection, and automated mitigation, an IPS significantly enhances overall network security.
In a zero-trust model, an IPS ensures that all network traffic is continuously monitored and verified, enhancing security at every access point.
Yes, IPS solutions can be scaled to fit the needs of small to large businesses, providing essential protection against cyber threats.
Challenges include ensuring compatibility with existing systems, managing false positives, and maintaining regular updates.
An IPS uses signature-based detection, anomaly detection, and behavioral analysis to identify and block malicious activities.