EyeQ Dot Net leads the way in advanced cybersecurity, protecting businesses globally. As your trusted defender, we shield you from emerging threats with cutting-edge solutions.


By mastering cyber security, you can protect your personal information, maintain the trust of your customers, and ensure the smooth operation of your business. Enrolling in a cyber security course can provide you with the skills needed to identify and mitigate potential threats, enhance your career prospects, and keep up with the latest advancements in technology. With the growing importance of digital safety, understanding 'what is cyber security' is not just beneficial but essential for anyone using the internet.
To fully understand what is cyber security, it's essential to recognize its various components, including network security, application security, and information security. Each element plays a critical role in defending against cyber threats and ensuring the secure operation of digital systems. Network security involves protecting the infrastructure from unauthorized access and attacks. Application security focuses on keeping software and devices free from threats. Information security is about safeguarding data integrity and privacy. Understanding what is cyber security also means being aware of cyber threat intelligence, risk management, and the importance of regular security audits. These practices help in identifying vulnerabilities and fortifying defenses against potential cyber-attacks.
By mastering cyber security, you can protect your personal information, maintain the trust of your customers, and ensure the smooth operation of your business. Enrolling in a cyber security course can provide you with the skills needed to identify and mitigate potential threats, enhance your career prospects, and keep up with the latest advancements in technology. With the growing importance of digital safety, understanding 'what is cyber security' is not just beneficial but essential for anyone using the internet.
In our increasingly connected world, understanding cyber security is more crucial than ever. Cyber attacks are becoming more sophisticated, targeting both individuals and organizations. The importance of cyber security cannot be overstated.
Effective cyber security helps prevent data breaches, financial loss, and reputational damage. Strong cyber security measures are essential for protecting sensitive information, such as personal data, financial records, and intellectual property. Business leaders can no longer solely rely on out-of-the-box cybersecurity solutions like antivirus software and firewalls; cybercriminals are getting smarter, and their tactics are becoming more resilient to conventional cyber defenses. Advanced cyber security strategies, including threat intelligence, incident response, and continuous monitoring, are critical for staying ahead of these evolving threats. It's important to cover all the fields of cybersecurity to stay well-protected.
Investing in cyber security provides numerous benefits. It ensures the privacy and security of your data, helps maintain customer trust, and supports business continuity. By understanding why cyber security is important, organizations can develop comprehensive security programs that address potential vulnerabilities and safeguard against a wide range of cyber threats. In today's digital age, prioritizing cyber security is not just a best practice but a necessity for long-term success and resilience.
By recognizing the importance of cyber security, businesses and individuals can proactively defend against malicious activities. Implementing a robust cyber security framework can lead to improved operational efficiency and reduced downtime caused by cyber incidents. It also helps in meeting regulatory requirements and avoiding legal penalties. Moreover, investing in cyber security training and awareness programs empowers employees to identify and respond to potential threats effectively. Ultimately, understanding why cyber security is important is key to fostering a culture of security that protects your digital assets and enhances overall trust and reliability in your organization.
To fully understand what are the divisions in cyber security, it’s essential to explore its various facets and the technologies involved. Cyber security encompasses several layers of protection spread across computers, networks, programs, and data. Here’s a deeper look into the key divisions in cyber security:
Network security involves measures to protect the integrity, confidentiality, and accessibility of data and network services. This includes:
Application security focuses on keeping software and devices free of threats. A compromised application can provide access to the data it’s designed to protect. Security measures include:
Information security protects the integrity and privacy of data, both in storage and in transit. Key strategies include:
Endpoints such as laptops, mobile devices, and desktops are often targeted by cyber attackers. Endpoint security involves:
With the increasing adoption of cloud services, securing cloud environments is critical. Cloud security measures include:
Understanding the divisions in cyber security is crucial for implementing a robust security strategy. Each division plays a unique role in safeguarding against different types of cyber threats. By mastering these divisions, you can better protect your digital assets and ensure comprehensive security across all layers of your IT environment.
Investing in understanding the divisions of cyber security brings significant benefits. It enhances your ability to identify and address specific security needs across various domains, improving your organization’s overall defense posture. With a clear grasp of network, application, information, endpoint, and cloud security, you can implement targeted strategies to mitigate risks, ensure compliance with industry regulations, and strengthen your overall security framework. This comprehensive approach not only protects against diverse cyber threats but also fosters a proactive security culture within your organization, safeguarding critical data and maintaining operational integrity.
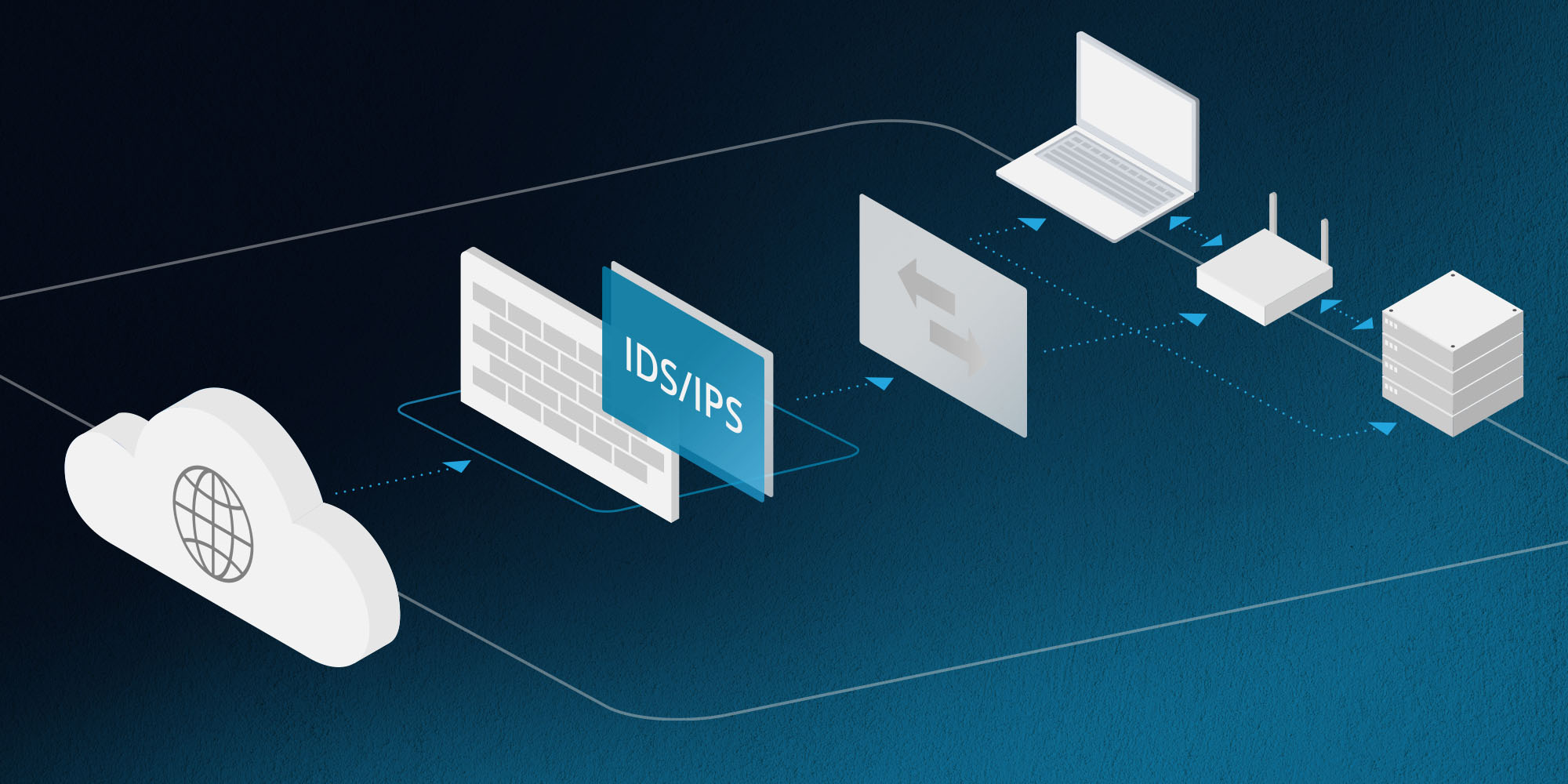
To safeguard against cyber threats, it's essential to follow best practices. Here are some key steps:
Compliance involves adhering to regulations and standards designed to protect data and ensure privacy. Security compliance is critical for safeguarding sensitive information from potential breaches and maintaining trust with stakeholders. To achieve compliance, organizations must implement specific security controls and measures, such as firewalls, encryption protocols, regular software updates, and recurring audits and assessments. These processes ensure that security controls are working effectively and that the organization meets its regulatory requirements.
Assessing current practices against regulatory requirements to ensure alignment.
Identifying and mitigating potential security risks to maintain compliance.
Implementing encryption and access controls to safeguard sensitive data.
Protects the privacy and personal data of EU citizens, mandating stringent data handling and protection practices.
Protects sensitive patient health information in the healthcare sector, enforcing privacy and security measures for health data.
Ensures secure handling of credit card information, requiring organizations to follow specific security protocols to protect payment data.
Understanding what security compliance entails is essential for any organization looking to protect sensitive information and avoid legal and financial repercussions. By adhering to these regulations and implementing robust security measures, organizations can ensure they meet industry standards, enhance their data protection strategies, and maintain operational integrity. The benefits of security compliance include reduced risk of data breaches, enhanced trust with customers, and avoidance of regulatory fines. Implementing a comprehensive security compliance program helps organizations proactively address potential vulnerabilities, meet legal obligations, and demonstrate a commitment to protecting sensitive data. Investing in security compliance offers several significant advantages. It not only minimizes the risk of costly data breaches but also enhances your organization’s reputation by showing a commitment to safeguarding customer information. A robust security compliance strategy can lead to better risk management, improved operational efficiency, and greater customer confidence. Moreover, staying compliant with industry regulations can streamline business processes and protect against legal liabilities. Embracing security compliance ensures that your organization remains resilient against evolving cyber threats and continues to thrive in a secure and regulated environment.A cyber security analyst is primarily responsible for protecting a company's network and systems from cyber attacks. The salary in India ranges between $ 3,575.37 to $ 13,348.04 with an average annual salary of $ 7,627.45

Penetration testers take a proactive, offensive role in cybersecurity by performing attacks on a company's existing digital systems. Penetration Tester salary in India ranges between $ 2,621.94 to $ 21,928.92 with an average annual salary of $ 9,415.13 Lakhs.

application security engineers anticipate structural vulnerabilities and determine how to correct them. Their work includes updating software, creating firewalls, etc. average salary in India is ₹9,00,000 per year, with a range of ₹6–17 lakhs.

A SOC analyst is a cybersecurity specialist who monitors an organization's IT infrastructure for threats. They are often the first responder in the battle against those threats. Average starting Salary in India is around ₹3.0 to ₹6.0 Lakhs per year.


Cyber security involves protecting systems, networks, and data from cyber attacks. It's crucial because it safeguards sensitive information and prevents financial and reputational damage.
Use strong passwords, enable two-factor authentication, keep software updated, and be cautious of phishing attempts.
Implement firewalls, use VPNs, regularly update software, conduct security training, and monitor network activity for unusual behavior.
EyeQ Dot Net Private Limited is providing the best cyber security intern trainee program around the world.
Encryption converts data into a coded format to protect it from unauthorized access during transmission and storage.
Look for suspicious email addresses, generic greetings, spelling errors, and urgent or threatening language prompting immediate action.
Benefits include enhanced security, automated threat responses, regulatory compliance, and reduced risk of data breaches.
Common attacks include phishing, malware, ransomware, denial-of-service (DoS), and man-in-the-middle (MitM) attacks.
Use strong, unique passwords for each account, enable two-factor authentication, avoid sharing personal information publicly, and use privacy settings on social media.
Yes, IPS solutions can be scaled to fit the needs of small to large businesses, providing essential protection against cyber threats.
Cyber security focuses on protecting systems and networks from digital attacks, while information security protects data from any form of threat, digital or physical.
Trends include the use of AI and machine learning for threat detection, increased focus on IoT security, and the development of quantum-resistant encryption.
Small businesses can improve security by conducting risk assessments, implementing basic security measures (e.g., firewalls, antivirus), and training employees on security best practices.
Immediately disconnect affected systems from the network, report the breach to the relevant authorities, and follow your organization's incident response plan.
Training helps employees recognize and respond to cyber threats, reducing the risk of breaches and enhancing overall security awareness.
Legal requirements vary by country and industry but often include data protection regulations like GDPR, HIPAA, and PCI DSS, which mandate specific security measures and reporting protocols.
Policies provide a framework for managing and protecting data, ensuring consistent security practices across the organization and compliance with legal requirements.
Social engineering exploits human psychology to gain access to systems or information, making it a significant threat that requires awareness and training to combat.
Use strong passwords or biometric authentication, install security updates, avoid downloading apps from unknown sources, and use mobile security software.
Firewalls act as barriers between trusted and untrusted networks, filtering traffic to prevent unauthorized access and attacks.
Cyber security focuses on protecting systems and networks from digital attacks, while information security protects data from any form of threat, digital or physical.
Firewalls act as barriers between trusted and untrusted networks, filtering traffic to prevent unauthorized access and attacks.