EyeQ Dot Net leads the way in advanced cybersecurity, protecting businesses globally. As your trusted defender, we shield you from emerging threats with cutting-edge solutions.


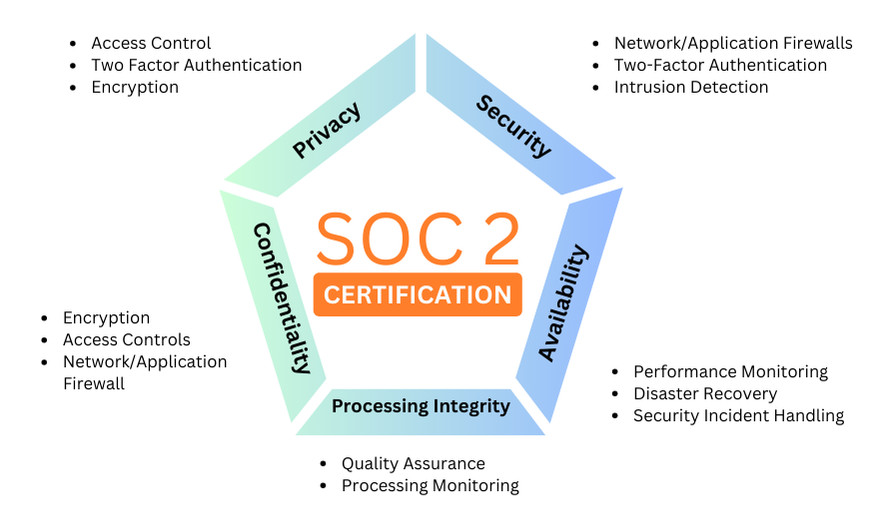
Developed by the American Institute of CPAs (AICPA), SOC 2 defines criteria for managing customer data based on five “trust service principles”—security, availability, processing integrity, confidentiality and privacy.
Achieving SOC 2 compliance provides a competitive edge in the marketplace, as it assures customers of the organization’s ability to meet industry-recognized standards for data protection and privacy.
The security principle refers to protection of system resources against unauthorized access. Access controls help prevent potential system abuse, theft or unauthorized removal of data, misuse of software, and improper alteration or disclosure of information.
The availability principle refers to the accessibility of the system, products or services as stipulated by a contract or service level agreement (SLA). As such, the minimum acceptable performance level for system availability is set by both parties.
This principle does not address system functionality and usability, but does involve security-related criteria that may affect availability. Monitoring network performance and availability, site failover and security incident handling are critical in this context.
The processing integrity principle addresses whether or not a system achieves its purpose (i.e., delivers the right data at the right price at the right time). Accordingly, data processing must be complete, valid, accurate, timely and authorized.
However, processing integrity does not necessarily imply data integrity. If data contains errors prior to being input into the system, detecting them is not usually the responsibility of the processing entity. Monitoring of data processing, coupled with quality assurance procedures, can help ensure processing integrity.
Data is considered confidential if its access and disclosure is restricted to a specified set of persons or organizations. Examples may include data intended only for company personnel, as well as business plans, intellectual property, internal price lists and other types of sensitive financial information.
Encryption is an important control for protecting confidentiality during transmission. Network and application firewalls, together with rigorous access controls, can be used to safeguard information being processed or stored on computer systems.
The privacy principle addresses the system’s collection, use, retention, disclosure and disposal of personal information in conformity with an organization’s privacy notice, as well as with criteria set forth in the AICPA’s generally accepted privacy principles (GAPP).
Personal identifiable information (PII) refers to details that can distinguish an individual (e.g., name, address, Social Security number). Some personal data related to health, race, sexuality and religion is also considered sensitive and generally requires an extra level of protection. Controls must be put in place to protect all PII from unauthorized access.
Although SOC 2 compliance isn't mandatory for SaaS and cloud computing vendors, it plays a crucial role in securing your data and building trust with clients.
EyeQ Dot Net ensures SOC 2 compliance by undergoing regular audits, meeting the five trust principles. Our compliance extends across all services, including web application security, DDoS protection, CDN content delivery, load balancing, and Attack Analytics.
SOC 2 Certification is essential for any service organization that handles sensitive client data, including SaaS providers, data centers, and cloud service providers.
Achieving SOC 2 Certification involves undergoing an audit by a licensed CPA firm to ensure compliance with the five trust principles.
The SOC 2 Certification process typically takes 6 to 12 months, depending on the organization’s preparedness and the scope of the SOC audit.
SOC 1 focuses on internal controls over financial reporting, while SOC 2 addresses controls relevant to security, availability, processing integrity, confidentiality, and privacy.
The cost of SOC 2 Certification varies widely depending on the size of the organization, the scope of the audit, and the auditing firm. It can range from $12,000 to $100,000.
SOC 2 Type 1 reports on the design of an organization's controls at a specific point in time, while SOC 2 Type 2 reports on the operational effectiveness of those controls over a period of time.
SOC 2 Certification needs to be renewed annually through a new audit to ensure ongoing compliance with the trust principles.
Benefits of SOC 2 Certification include enhanced trust with clients, competitive advantage, improved data security, and compliance with regulatory requirements.
Yes, small businesses can achieve SOC 2 Certification. It demonstrates their commitment to data security and can be a significant differentiator in the marketplace.
SOC 2 Certification assures clients that their data is handled securely and in accordance with industry standards, fostering trust and transparency in the service provider.
VAPT helps organizations achieve compliance with various industry standards and regulations such as PCI DSS, HIPAA, GDPR, and ISO 27001. Regular VAPT assessments ensure that security controls are in place, vulnerabilities are addressed, and risks are mitigated, helping organizations meet the required security benchmarks and avoid penalties.
Outsourcing VAPT services to a professional provider offers several benefits: Expertise:Access to skilled security professionals with extensive experience. Objectivity:An unbiased assessment of your security posture. Advanced Tools:Use of cutting-edge tools and methodologies. Time and Cost Efficiency:Saves time and resources compared to in-house efforts. Comprehensive Reporting:Detailed and actionable reports with prioritized remediation steps. Continuous Support:Ongoing support and guidance to maintain and improve security measures.
